The Guy Who Invented Those Annoying Password Rules Now Regrets Wasting Your Time
http://gizmodo.com/the-guy-who-invented-those-annoying-password-rules-now-1797643987
Simple math shows that a shorter password with wacky characters is much easier to crack than a long string of easy-to-remember words. This classic XKCD comic shows how four simple words create a passphrase that would take a computer 550 years to guess, while a nonsensical string of random characters would take approximately three days:
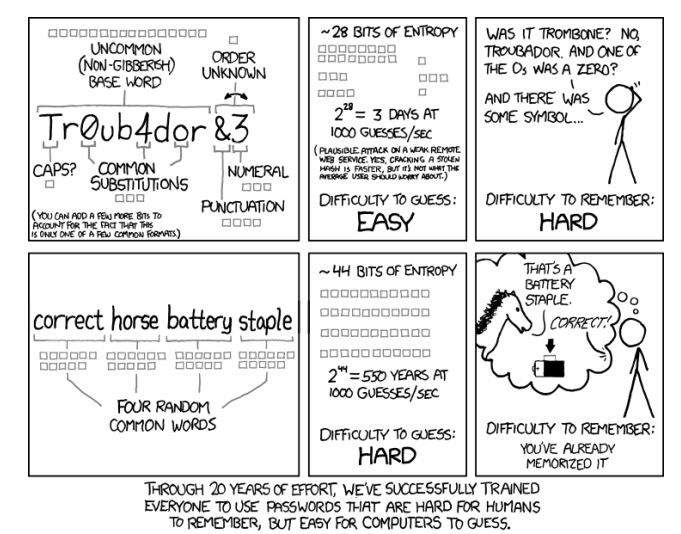
Simple math shows that a shorter password with wacky characters is much easier to crack than a long string of easy-to-remember words. This classic XKCD comic shows how four simple words create a passphrase that would take a computer 550 years to guess, while a nonsensical string of random characters would take approximately three days:



Comments
I always thought that was better than the typical random character password. Many servers today still won't accept more than 12 or 14 characters for the password string, which is only enough for two medium-length words.
Of course remembering what part number went with what site is another matter altogether.
We never fell for it anyway
On sites that are fussy about adding numbers and punctuation I end up with:
notSoCommonPhrase1!
Shouldn't we be using Unicode user names and passwords now? Just to add to the madness.
My issue with complex passwords is mobile devices, it's hard to retain that muscle memory on a tiny little keyboard. I use a combination of words and randoms, but it's not the 1337 speak stuff.
I don't like security questions much, I always put fake answers that are unique to the site questing them. I'd rather not have that information stolen along with all of the other information. Seems kinda silly to give that information up. It can also be funny if you're asked the question over the phone, I get a lot of laughs at the answers to my security questions.
But lots of wi-fi routers accept pass phrases with spaces, it's just that most people don't know that.
DEC!vis1fish2yu
Even with short words you eadily get long passwords. If you pick language with diferent roots they'll come out even beter
Why must a account to a forum be protected by a hyper secure password at all?
Or my electricity bill at PG&E?
I could write a letter to some congress-man, using your name and address, even sign it with whatever signature. Nothing protected by passwords.
My bank-card is protected by lousy 4 numbers, but to log into SourceForge I need "no spaces, a minimum of upper/lower case, numbers, and/or punctuation characters".
isn't that just silly?
Mike
There is no substitution:
vis (Dutch) = fish (English) = yu (Chinese)
the beauty is i only need to remember one word
anyway it works for me
That's true, but to do anything with those four numbers (PIN) they need your card. Maybe that's what we're missing in computer authentication: physical evidence it's us. A little pin-prick blood analyzer would probably do the trick.
2^28 = 3 days at 1000 guesses a second....
What?
Why would any software allow anyone to enter 1000 passwords a second?
Its obviously not a human forgotten his password.
I would have thought two a minute tops, and access denied/banned after 5 fails.
Surely thats an OBVIOUS hacking attempt- any password verifying software OUGHT to be checking for this. This is the 21st century- or is it beyond the whit of current systems.
Or is it the result of the 'cloud' that cant be protected against this- if so. perhaps it needs to be changed.
Dave
Blargons.frozzles
They spell like they sound, aren't in a dictionary, nobody types them.
Maybe by then they will have notified you that they were hacked and you can change your password.
Mike
However nobody should be storing passwords in a plain text readable form. They should be scrambled. Store a hash of the password not the actual password. A large gob of random "salt" should be added to the password before hashing, thus making it very hard to get the password from the hash. The hash function should be cryptographically secure. e.g. use Bcrypt.
With these commonly known procedures in place it's not worth any ones time to try and get passwords out of the password database they have acquired. Even if short simple passwords are used.