Building an OTP Key Generator.
virtuPIC said...
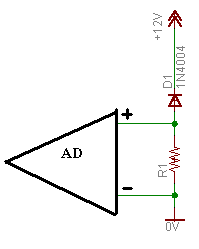
If you want to produce reasonable, uniformly distributed real random numbers you should use a little external hardware which employs quantum effects. No, I don't mean a radioactive sample with Geiger counter. Would work - but would be rather expensive. But what else? You can simply take a diode or part of transistor give it a high backward voltage and measure the current. There will be noise that is real quantum-random.
My thinking is shield the random number generator to minimize any effects from outside noise. Keep only the least significant bit of he voltage across the resister.
Was thinking to use this AD; http://focus.ti.com/lit/ds/symlink/ads1225.pdf
would take almost a year though to generate a 2GB key file.
Outside of the randomness was thinking use a propeler and 2 uSD cards to store the key. uSD because it is smaller and easier to smugle.
Anyone know if I am on the right track and how acurate an ad convert would be needed? 200 days is to long to wait to generate the keys. 1 to 7 days would be good. 8-30 pushing it but ok.
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Need to make your prop design easier or secure? Get a PropMod has crystal, eeprom, and programing header in a 40 pin dip 0.7" pitch module with uSD reader, and RTC options.


Comments
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Need to make your prop design easier or secure? Get a PropMod has crystal, eeprom, and programing header in a 40 pin dip 0.7" pitch module with uSD reader, and RTC options.
Well, it's more breaking olds. Wikipedia is your friend.
In brief: There is only one incrackable cryptosystem. The one time pad. That's the OTP in the subject. Each bit is encrypted separately and no key will be recycled.To encrypt a single message bit you need one key bit. The key is as long the message.
To generate such a key sequence you need uncorrelated real random data of equal distribution over {0,1}. If an attacker gets a transmitted message and the key used for this transmission he cannot use it to crack any other transmission since there is a key change to a completely unrelated key.
As I already wrote in another thread, I would only use 1 bit ADC. I don't know how you call it - anyway, the shot through a bipolar junction is a binary quantum effect. Many of them happen and your lines and your ADC will low pass filter them. There is no need to care for several bits. However, the comparator implementing the 1 bit ADC should be sensitive enough to find the signal. I don't know whether the logic CMOS input fulfills this.
And regarding the speed: If you use a fast comparator (look at www.ti.com you can get the bits as fast as you can shift them.
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Airspace V - international hangar flying!
www.airspace-v.com/ggadgets for tools & toys
Not sure if you will need the Schmitt trigger on the way into the Prop.
He seems to be getting 10,000 random bits per second or about 1Gb per day.
Don't forget to unbias the output, you may have more ones's than zeros or vice versa.
Like so "To unbias the bits, I use the Von Neumann method, described in the Schneier red book (Applied Cryptography 2nd Ed.) on page 425. I sample two bits and discard them if they are equal. If they are not equal, then I accumulate one of the bits. When enough bits are accumulated, I output them"
I'd be inclined to drive the transistors from a separate battery supply for isolation and shield battery and transistors together.
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
For me, the past is not over yet.
Here's a 2 channel ADC which will give you 24-bit samples at 96Khz. Last time we bought these they were ~$5 each. It may be more complicated than you want to deal with. It needs a clock whereas the one you posted didn't. However at nearly 100x the speed of the one you posted it, it might be worth it. We actually run these at 80Khz, which allows the PASM to read both channels in one cog. I can share some code for these if you are interested.
pgb
to make sure noise is at a minimum on power I will use several 0.1uF caps near rails and a 12v supper cap after each regulator.
traces will be identical to both collectors
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Need to make your prop design easier or secure? Get a PropMod has crystal, eeprom, and programing header in a 40 pin dip 0.7" pitch module with uSD reader, and RTC options.
Actually the technique of sampling two bits was supposed to be two consecutive bits from one circuit. You should do a search for "Von Neumann method" to see what it is all about.
I can't quite convince myself that taking the two bits from two separate circuits is equivalent. Might be.
Hmm.. what if one circuit is in the middle of a long string of ones. Then every time the second circuit produces a 0 you would accept a bit because they are different. Doesn't seem quite right to me.
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
For me, the past is not over yet.
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Need to make your prop design easier or secure? Get a PropMod has crystal, eeprom, and programing header in a 40 pin dip 0.7" pitch module with uSD reader, and RTC options.
Now the question is this: if an attacker knew what m and n were, would that be enough of a clue to get a handle on the OTP?
-Phil
for space reasons I would not use ascii but instead a variable bit length coding system. uses less space
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Need to make your prop design easier or secure? Get a PropMod has crystal, eeprom, and programing header in a 40 pin dip 0.7" pitch module with uSD reader, and RTC options.
You should include a check for the total failure of your generator. For example in the circuit I posted if the 12v supply drops too low the randomness suddenly stops. I forget the threshold voltage I found with my transistors.
If you are using the Von Neumann method on successive bits from a single generator this is not a problem as there will then be no output, it will just be sitting there waiting for bits to change. Perhaps you would have a time out so that the user of the random bits is not waiting for ever but gets an error return.
If you are comparing two bits from two generators you would be in trouble if one is stuck 1 and the other is stuck 0. The un-biassing would always return the same 1 or 0.
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
For me, the past is not over yet.
the strength of encryption should be the same. we should assume the thef knows everything but the key and original message.
that said xor with static number would be useless. are only strength is in the quality of key we generate.
quality means true random with no cyclic repetition from things like 60hz hum or supper long repeating bits leaving essentially unencrypted. to many restrictions on random also weakens
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Need to make your prop design easier or secure? Get a PropMod has crystal, eeprom, and programing header in a 40 pin dip 0.7" pitch module with uSD reader, and RTC options.
However, if you stick to the true randomness (and lets assume our generator is) then you have to accept the fact that long runs of ones or zeros can happen. Albeit rarely. Selecting from the incoming bits in any way, to remove long runs say, is breaking the rules.
Chip says we don't need any external circuitry to do this on the Propeller.
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
For me, the past is not over yet.
I will use the real random to generate a test file and upload to my server for people to analyze.
not worrying about pins because key generator and encryptor are not same device
yes stopping real long runs does remove combinations but my suggestion of 12 max only removes 2 in 8 billion
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Need to make your prop design easier or secure? Get a PropMod has crystal, eeprom, and programing header in a 40 pin dip 0.7" pitch module with uSD reader, and RTC options.
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Need to make your prop design easier or secure? Get a PropMod has crystal, eeprom, and programing header in a 40 pin dip 0.7" pitch module with uSD reader, and RTC options.
using variables bit length character also adds security as you don't know where char starts without knowing from beginning. should be at least one 1 before a long run in any message.
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Need to make your prop design easier or secure? Get a PropMod has crystal, eeprom, and programing header in a 40 pin dip 0.7" pitch module with uSD reader, and RTC options.
Whatever you do check out the Diehard random number tests stat.fsu.edu/pub/diehard/
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
For me, the past is not over yet.
MCVBEET1(Matthew Cornelisse Variable Bit English Encoding Table 1)
0 10000000110
1 10000000000100
2 10000000000101
3 10000000000110
4 10000000000111
5 10000000000001
6 10000000001100
7 10000000001101
8 10000000001110
9 10000000001111
A 1011
B 000001
C 01001
D 10101
E 111
F 00010
G 100011
H 0110
I 1101
J 1000000111
K 1000001
L 10100
M 00001
N 1100
O 1001
P 100001
Q 1000000010
R 0101
S 0111
T 001
U 01000
V 000000
W 00011
X 1000000110
Y 100010
Z 1000000001
$ 10000000000010
% 10000000000011
, 100000001111
. 100000000010
space 100000010
shift 100000001110
caps 100000000000000001
Enter 100000000000001
End 1000000000000001
ASCII 10000000000000001
UNICODE 100000000000000000
To encode a message pick the bit pattern to the letter you want. Letters are lower case unless following a period.· shift preceding a symbol changes its normal state.· all are capitalized if between to cap symbols
To decode start at first bit and find bit patern in table that matches. remove that section and continue.
In general this table gives smaller file sizes then ASCII. Also because of the variable bit length property you can't just start decoding in the middle of a message making it more secure in an OTP like encryption.
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Need to make your prop design easier or secure? Get a PropMod has crystal, eeprom, and programing header in a 40 pin dip 0.7" pitch module with uSD reader, and RTC options.
Post Edited (mctrivia) : 4/12/2009 8:27:46 PM GMT
-Phil
In ASCII seomething like 'wrnpois.nop indv' means that the key has not been found. If the attacker gets 'Hello, wolrd!' chances are high that the key has been found. In other terms, if your plaintext language has high redundancy then an attacker knows if an attempt gave a sensible decryption. If your plaintext language has no redundancy then all possible bit sequences are sensible and the attacker doesn't know if it was a success.
Compression reduces the redundancy. Most of the possible bit sequences are valid and sensible. If you have a few characters of English text in ASCII you only get very few sensible texts. But be aware that many compression programs add fixed headers that can be used to attack your cipher!
By the way, do you know the Q-codes? There have been abbreviations used at least in second world war to compress clear text. A few of them are still used - also in civilian context. For instance in aviation QNH is still used for something like 'pressure comverted to medium sea level in hPa' used for altimeter setting. Quite a compression factor. You know of Enigma? The German crypto engine cracked by a British group around Alan Turing? They did something unusual when observed to provoke transmission in clear text (read: without compression). Something like shooting seals (I mean the animals) lying on a beach...
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Airspace V - international hangar flying!
www.airspace-v.com/ggadgets for tools & toys
also longest symbol is 34 bit 18+16 bit unicode symbol
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Need to make your prop design easier or secure? Get a PropMod has crystal, eeprom, and programing header in a 40 pin dip 0.7" pitch module with uSD reader, and RTC options.
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Airspace V - international hangar flying!
www.airspace-v.com/ggadgets for tools & toys
meant for sending plain text messages. I would include a crc for error checking but if that is encrypted with otp it will not help an attacker.
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Need to make your prop design easier or secure? Get a PropMod has crystal, eeprom, and programing header in a 40 pin dip 0.7" pitch module with uSD reader, and RTC options.
If you're really worried about the security of your data, don't use just one method (like only AES-128 only...).
Also:
Take a look at polymorphic ciphers too...
-Tim
P.S. To your initial point, don't smuggle an SD card with a key... The best idea is to do some form of stenography (embed the key data in another file type (like the LSB of a large bitmap - with no encoding!!! STools does this but leaves a finger-print that investigators are already looking for). You can also place the key in a hidden partition on a drive for plausible-deniabillity... If you get caught with an SD card hidden in your shoe or something, you're more likely to be compelled to reveal the contents. If a key-file was hidden in a picture, that looked like every other picture that was in a folder (and wasn't something awful like kiddy-porn), in most cases even if you were asked to show the contents of a file folder on a thumb-drive, the investigator wouldn't likely have enough probable cause to look further at the files (this may not matter if you are on a watch list though). -T
Post Edited (GreyBox Tim) : 4/13/2009 6:03:34 AM GMT
not that I would go that far since legal here
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Need to make your prop design easier or secure? Get a PropMod has crystal, eeprom, and programing header in a 40 pin dip 0.7" pitch module with uSD reader, and RTC options.
BTW, are we running off topic here? What was the original question? The subject tells something about an OTP key generator...
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Airspace V - international hangar flying!
www.airspace-v.com/ggadgets for tools & toys
yes off topic but related
I generated a 126MB file during my shift today.
I have attached the diehard results of this file. in what I see it looks pretty good. Actual file will be available here as soon as it is done uploading. Currently at 29% Will probably finish by the end of the next hour(7PM MDT)
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Need to make your prop design easier or secure? Get a PropMod has crystal, eeprom, and programing header in a 40 pin dip 0.7" pitch module with uSD reader, and RTC options.
Post Edited (mctrivia) : 4/18/2009 11:51:55 PM GMT
OPERM5 test for file otp00000.bin
For a sample of 1,000,000 consecutive 5-tuples,
chisquare for 99 degrees of freedom= 72.793; p-value= .022276
OPERM5 test for file otp00000.bin
For a sample of 1,000,000 consecutive 5-tuples,
chisquare for 99 degrees of freedom= 81.191; p-value= .096333
upload of base data is now done.
▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔▔
Need to make your prop design easier or secure? Get a PropMod has crystal, eeprom, and programing header in a 40 pin dip 0.7" pitch module with uSD reader, and RTC options.
Post Edited (mctrivia) : 4/19/2009 12:56:46 AM GMT