Anybody know what this is all about?
 Phil Pilgrim (PhiPi)
Posts: 23,514
Phil Pilgrim (PhiPi)
Posts: 23,514
Just ran across this warning in Chrome on my MacBook:
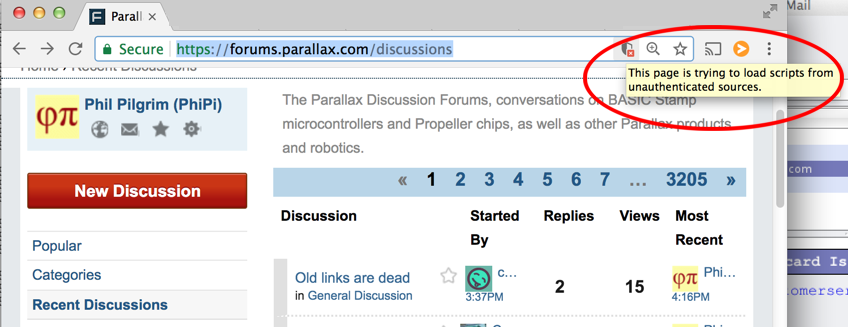
I'm sure it's benign, but I do wonder what was being blocked.
-Phil

I'm sure it's benign, but I do wonder what was being blocked.
-Phil


Comments
https://support.google.com/chrome/answer/99020?co=GENIE.Platform=Desktop&hl=en
Not real helpful though - "The site you're visiting is not secure."
EDIT: You can turn it off in settings "Protect you and your device from dangerous sites" under Advanced "Privacy & Security"
Used to be that if the web site you visited was secured with HTTPS it could fetch resources, Javascript etc, over the non-secure HTTP. This basically destroys any security you think you have by using HTTPS.
At least Chrome now a days complains when that happens. Warning you about the security hole. Perhaps other browsers have caught up with this idea, I have not checked for ages.
Seems odd the page is trying to download that jQuery from http://ajax.googleapis.com/ajax/libs/jquery/1.7.2/jquery.min.js when it has already downloaded jQuery from https://forums.parallax.com/js/library/jquery.js?v=2.1.11
I'd also rather this site did not partake in facebooks tracking of visitors with https://staticxx.facebook.com/connect/xd_arbiter/r/hsBwMj6iLmk.js?version=42 That link leads to this:
SECURITY WARNING: Please treat the URL above as you would your password and do not share it with anyone. See the Facebook Help Center for more information.
Then there is this other link in the page to a sneaky one pixel image served by facebook for tracking purposes: https://www.facebook.com/impression.php/f302cbbe4608974/?lid=115&payload={"source":"jssdk"}
It's a pretty poor show that we have been complaining about for ages.
http will become obsolete or used for non important data. (IOT)
https everywhere. GET IT.
This addon will help your browser choose the https urls if they can, when connecting to a http address. (yes, it will try the https version of the url first, even if the html links the http url)
https://www.eff.org/https-everywhere
THANKS EFF!
-Phil
If you mean the Parallax Website, they use Drupal for their CMS, not WordPress. The forum uses Vanilla, also open source, but not WordPress-based.
Officially jQuery is provided on a number of content delivery networks, Google being one of them. The "official" ones all have alternative https: access. I'm not sure why the forum pages have both local and CDN access to jQuery (different versions at that), but it's also possible to create mixed-protocol pages to avoid the warning.
It's a bad idea.
It's like locking your front door and ignoring somebody who tells you that you have left the back door and all the windows open!